Overview:
- This Prototype authenticates using the local authentication database. The stubs are in place for federated identity via saml, etc. Access control is based on attributes provisioned to ViewDS All access rules and their evaluation is external
-
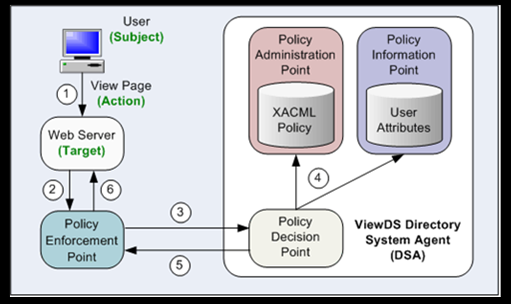
-
The steps shown in the illustration are as follows:
- A user attempts to view a web page hosted by a web server.
- The web server asks the Policy Enforcement Point (PEP) to form an 'authorization decision request'.
- The PEP sends the 'authorization decision request' to the Policy Decision Point (PDP). The authorization decision request includes XACML attributes that identify, among other things, the user and the web page they are attempting to access (see XACML attributes provided by an HTTP PEP).
- The Policy Decision Point (PDP) determines whether access should be permitted. It does so by accessing the appropriate XACML policy. The policy instructs the PDP to consider which web page is being accessed and by which user. The user is identified according to directory attributes in the Policy Information Point (PIP).
- The PDP returns an 'authorization decision response' to the PEP.
- The web server acts on the decision to permit or deny access to the web page.
